Domain Name Server (dns) Based Layer Attacks
ICANN currently grants permission to organizations to act as domain name registrars for specific higher level domains. A method apparatus and program product utilize Domain Name Service DNS prefetching in a recursive DNS server eg to mitigate Distributed Denial of Service DDoS attacks on a DNS service.
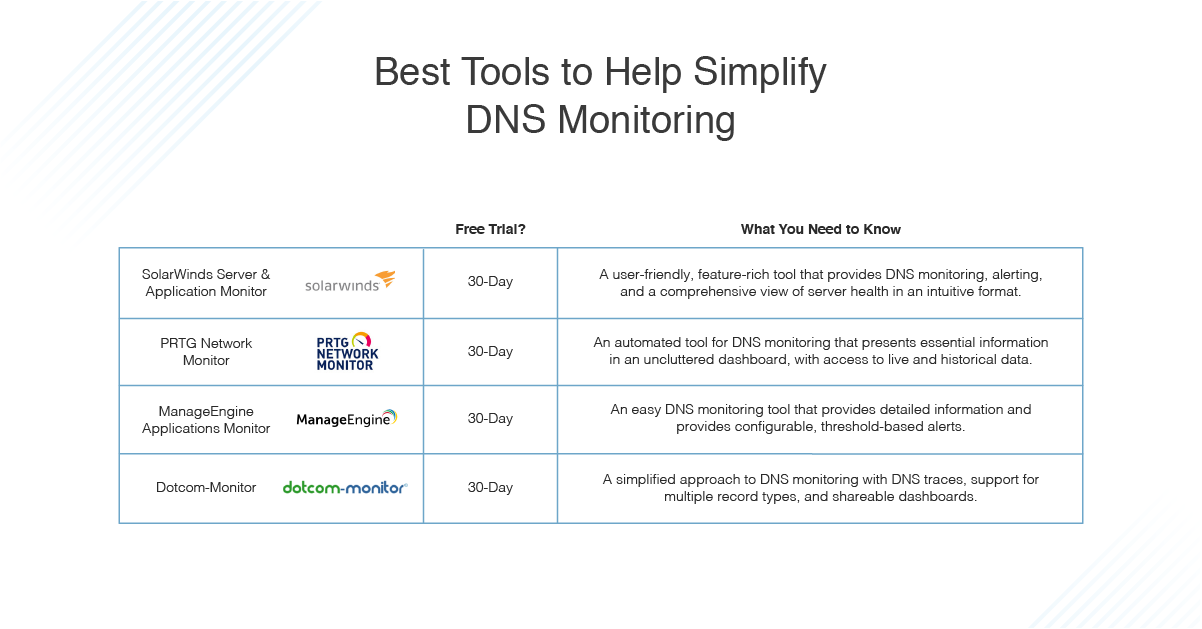 How To Use Nslookup And List Of Best Dns Monitoring Tools Dnsstuff
How To Use Nslookup And List Of Best Dns Monitoring Tools Dnsstuff
In other cases these attackers will try to determine vulnerabilities within the system itself and exploit them for their own good.

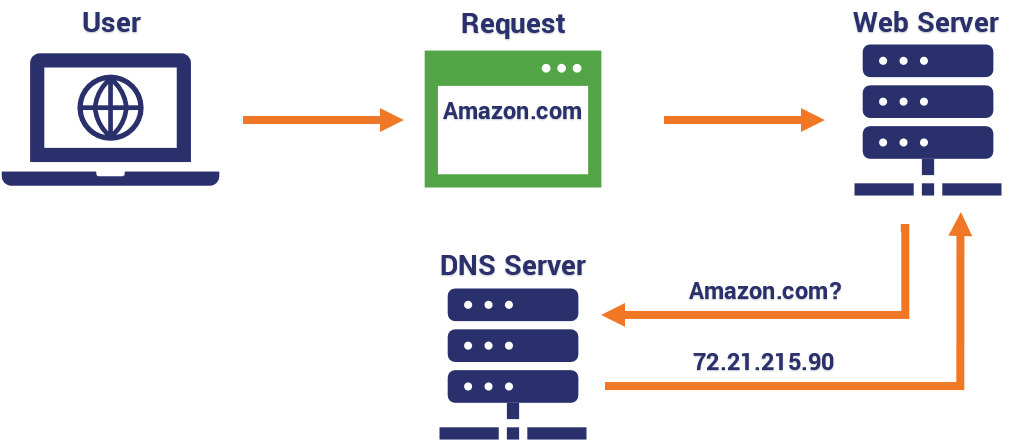
Domain name server (dns) based layer attacks. And the name server returns the IP address corresponding to that domain name to the host so that the host can future connect to that IP address. Authoritative nameserver - This final nameserver can be thought of as a dictionary on a rack of books in which a specific name can be translated into its definition. A domain name server DNS attack is a cybercrime that probes these servers looking for weaknesses to exploit.
Domain Name System record types. This results in traffic being diverted to the attackers computer or any other computer. Specifically the recursion feature essentially acts as a middle man between consumers and the DNS servers hosting a companys domains and IP addresses.
By exploiting system vulnerabilities attackers will try to inject malicious data into your DNS resolvers cache. The authoritative nameserver is the last stop in the nameserver query. If a user is unable to find the phonebook it cannot lookup the address in order to make the call for a particular resource.
21 Oct 2020 Over the past few years domain name system DNS attacks have emerged as one of the most common and dangerous cyber security threats faced by businesses. DNS resource exhaustion attacks can clog the DNS infrastructure of ISPs blocking the ISPs customers from reaching sites on the internet. In DNSSEC if a name server determines that the address record for a given domain has not been modified in transit it resolves the domain and lets the user visit the site.
DNS Domain Name System Name service in Internet Zone is an administrative unit domain is a subtree. The trick in this kind of attack is pretty easy to understand. Simply put a DNS poisoning attack compromises DNS servers so visitors who try to go to a website are secretly routed to the wrong IP address behind the scenes.
This can be done by attackers registering a domain name. Like a phone book the name server is a collection of domain names matched to IP addresses. The hackers goal is to hamper resolution of resource records of the zone and its sub-zones.
If the authoritative name server has access to the requested record it will return the IP address for the requested hostname back to the DNS Recursor the. Some of the most common types of DNS attacks are the DDoS attack DNS rebinding attack cache poisoning Distributed Reflection DoS attack DNS Tunneling DNS hijacking basic NXDOMAIN attack Phantom domain attack Random subdomain attack TCP SYN Floods and Domain lock-up attack. A DNS flood is a type of distributed denial-of-service attack DDoS where an attacker floods a particular domains DNS servers in an attempt to disrupt DNS resolution for that domain.
In order to understand how DNS attacks work it is important to first understand how the domain name system works. DNS cache poisoning also known as DNS spoofing is one of the most common DNS attacks that happen every day. How DNS-Specific Attacks Work.
In DNS attacks hackers will sometimes target the servers which contain the domain names. DNS-Specific Attacks DNS-specific attacks are also referred to as NXDomain attacks where the attacker targets one or more domain name system server s belonging to a given zone. A DNS attack is an exploit in which an attacker takes advantage of vulnerabilities in the domain name system DNS.
A DNS name server is a server that stores the DNS records for a domain. If however that record. Adversaries may communicate using the Domain Name System DNS application layer protocol to avoid detectionnetwork filtering by blending in with existing traffic.
When hackers take advantage of vulnerabilities in the Domain Name System DNS we call this a DNS attack. By managing domain name reservations name registrars are critical to how DNS works. Denial of service DoS An attack where the attacker renders a computer useless inaccessible to the user by making a resource unavailable or by flooding the system with traffic.
DNS spoofing also referred to as DNS cache poisoning is a form of computer security hacking in which corrupt Domain Name System data is introduced into the DNS resolvers cache causing the name server to return an incorrect result record eg. The most common types of records stored in the DNS database are for Start of Authority SOA IP addresses A and AAAA SMTP mail exchangers MX name servers NS pointers for reverse DNS lookups PTR and domain name aliases CNAME. Once in they can change coding or other information.
A DNS name server responds with answers to queries against its database. Commands to the remote system and often the results of those commands will be embedded within the protocol traffic between the client and server. Name to Address Resolution The host request the DNS name server to resolve the domain name.
And the name server returns the IP address corresponding to that domain name to the host so that the host can future connect to that IP address. DNS amplification attacks DNS has a recursion feature that permits domain name resolution to be handed off to more powerfully built sites. Name to Address Resolution The host request the DNS name server to resolve the domain name.
DNS Domain Name System Name service in Internet Zone is an administrative unit domain is a subtree.
 Dns Basics And Building Simple Dns Server In Go By Mohan Prasath Medium
Dns Basics And Building Simple Dns Server In Go By Mohan Prasath Medium
 The Tcp Ip Protocol Suite Includes Many Protocols As Shown In Figure Below Each Layer Has O Networking Basics Communication Process Cybersecurity Infographic
The Tcp Ip Protocol Suite Includes Many Protocols As Shown In Figure Below Each Layer Has O Networking Basics Communication Process Cybersecurity Infographic
 Dns Poisoning Attacks A Guide For Website Admins Security Boulevard
Dns Poisoning Attacks A Guide For Website Admins Security Boulevard
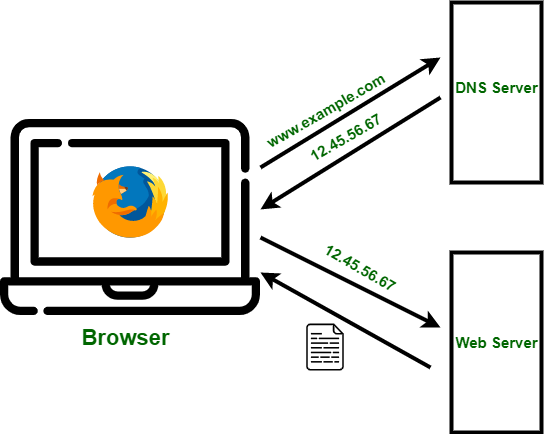 Working Of Domain Name System Dns Server Geeksforgeeks
Working Of Domain Name System Dns Server Geeksforgeeks
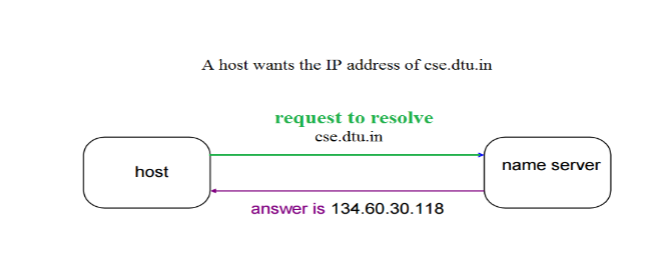 Domain Name System Dns In Application Layer Geeksforgeeks
Domain Name System Dns In Application Layer Geeksforgeeks
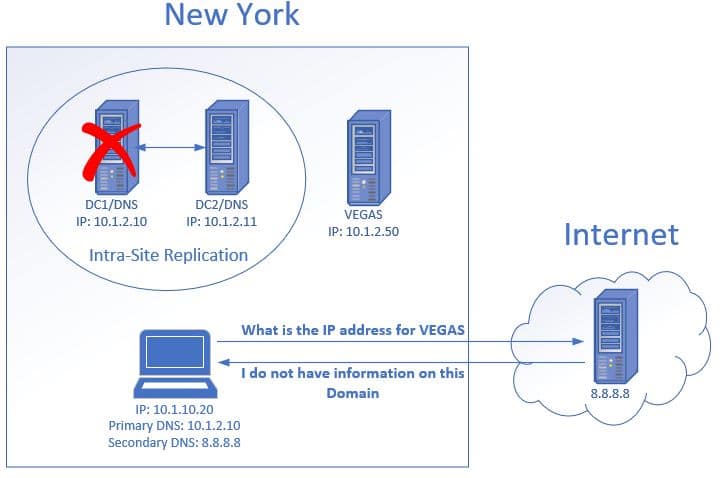 Dns Best Practices The Definitive Guide
Dns Best Practices The Definitive Guide
 How To Minimize The Dos Attack Impact Ddos Attack Denial Of Service Attack 3 Network
How To Minimize The Dos Attack Impact Ddos Attack Denial Of Service Attack 3 Network
 Dns Domain Name Server Networking Name Server Domain Server Dns
Dns Domain Name Server Networking Name Server Domain Server Dns
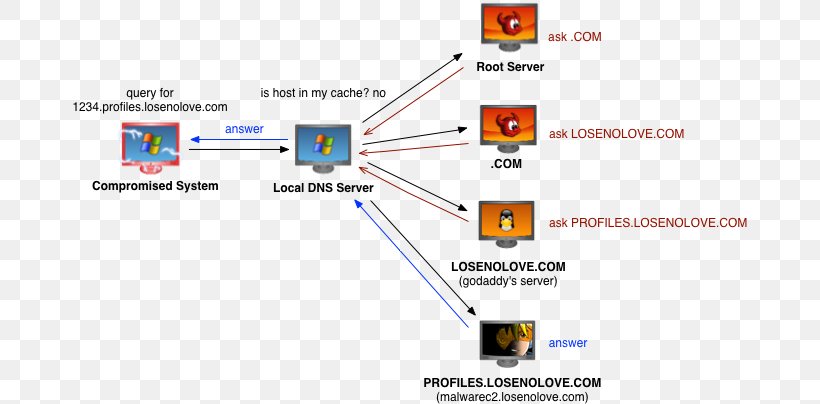 Domain Name System Port Name Server Ip Address Dynamic Dns Png 676x404px Domain Name System Area
Domain Name System Port Name Server Ip Address Dynamic Dns Png 676x404px Domain Name System Area
 What Is Domain Name System Dns Filtering Top Cloud Solutions Provider Avatara
What Is Domain Name System Dns Filtering Top Cloud Solutions Provider Avatara

 Dns Security From Comodo Dns Security Security Solutions
Dns Security From Comodo Dns Security Security Solutions

 Dns Client Service Architecture Dns Network Infrastructure Information And Communications Technology
Dns Client Service Architecture Dns Network Infrastructure Information And Communications Technology

Https Jsssjournal Com Article Download 3660
 Dns Server Service Architecture Dns Network Infrastructure Name Server
Dns Server Service Architecture Dns Network Infrastructure Name Server
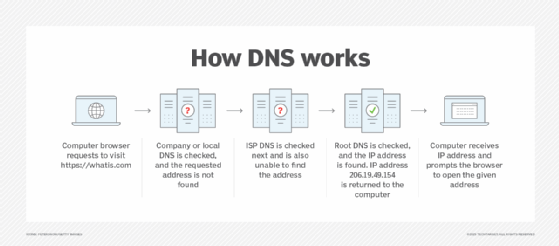
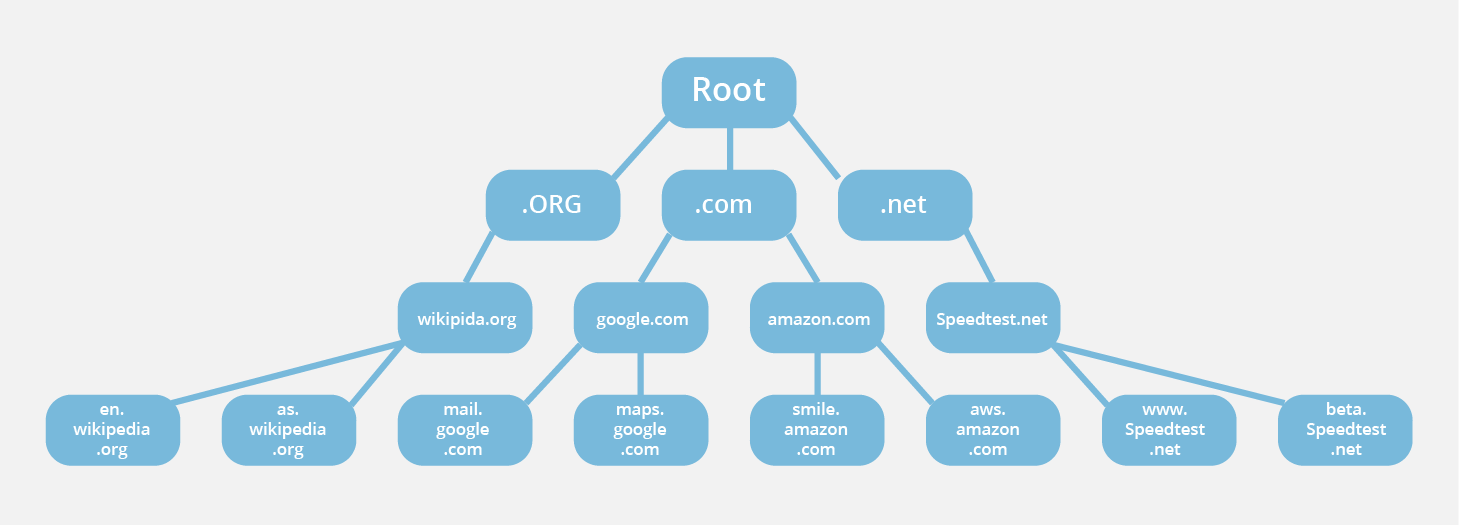
Post a Comment for "Domain Name Server (dns) Based Layer Attacks"